CICS Pseudo - Conversational Programs: The Timeless Masterpiece of Mainframe Processing
Captain Uday Prasad
In the world of enterprise computing, CICS (Customer Information Control System) stands as a true powerhouse — renowned for its unmatched reliability, efficiency, and decades-long legacy. Developed by IBM in the 1960s, CICS has not only survived but thrived, continuing to drive the high-transaction operations of industries like banking, telecommunications, and beyond. At the core of its ongoing success lies the often-overlooked gem of pseudo-conversational programming. This ingenious design allows CICS to process vast volumes of transactions with incredible speed and flexibility, making it an enduring leader in the world of enterprise systems.
For those new to mainframe development or those immersed in the world of open systems and cloud computing, pseudo-conversational programs may seem like a relic of a bygone era. However, this programming model is one of the main reasons CICS remains at the forefront of transactional computing even today, powering more than 90% of ATMs globally. It is a testament to the enduring power of good design and thoughtful architecture.
This article explores the core concepts of CICS pseudo-conversational programs, their unique characteristics, and the reasons behind their ongoing relevance in a world enamored with "modernization" and cloud computing.
What is a Pseudo-Conversational Program?
A pseudo-conversational program in CICS is a type of program designed to break the interaction between the user and the system into small, discrete tasks. Instead of keeping the program running continuously, the program performs a task, then temporarily gives up control and stops the task before being resumed later. A transaction is the execution of a series of tasks. Each task is a small unit of work that starts, completes its assigned job, and then ends.
Thus
Transaction = Task1 + Task2 + Task3 +………………………........................+ Taskn
Multi-Tasking vs multi-programming
In CICS, while multiple users can invoke the same transaction, each user is given a separate task
For a program to run in a pseudo-conversational manner, it must be re-entrant and capable of multi-programming. To understand this, let's first explore multi-tasking.
Multi-tasking refers to the operating system's ability to execute multiple tasks concurrently, whether those tasks involve one or several programs. CICS supports multi-tasking within its own region, meaning that multiple CICS tasks can run simultaneously.
Now, let's move on to multi-threading.
Multi-threading refers to the ability of the operating system to allow tasks to share the same program in a multi-tasking environment. A program that is involved in multi-tasking must be re-entrant. A re-entrant program is one that doesn't modify itself, allowing it to re-enter and continue processing after an interruption or temporary pause. On the other hand, a non-re-entrant program modifies itself, making it unable to re-enter or continue after being interrupted. Batch programs are typical examples of non-re-entrant programs, while online programs rely on re-entrant programs.
In CICS, a re-entrant program is often referred to as a quasi-re-entrant program. This allows the program to re-enter itself repeatedly without modification, even if CICS interrupts or stops the task. CICS ensures quasi-reentrancy automatically when executing a command-level COBOL application program. For each task, CICS allocates a unique copy of the program’s working storage section. If the program modifies itself during task execution, the changes are stored in the Task Global Table (TGT), which is a part of the program. Since CICS assigns a unique TGT to each task, when another task is initiated using the same program, it will use the original (unaltered) program. This ensures that CICS programs achieve quasi-reentrancy automatically, allowing for efficient and concurrent task processing without interference.
This methodology contrasts with traditional conversational programming, where a continuous, interactive conversation happens between the user and the system during the entire execution.
In a pseudo-conversational environment, the program doesn't remain in memory for the entire duration of the user's interaction. Instead, it is re-invoked or re-entered from a point of recovery after each task is completed. This mechanism allows the program to be much more efficient in managing system resources, making it possible to handle thousands of concurrent users with minimal system load.
How Pseudo-Conversational Programs Work?
1. Task Processing and State Preservation: In a CICS pseudo-conversational program, the application does not need to remain resident in memory between requests. Each time the program completes a task, it returns control to CICS, which stores the necessary data (such as transaction state, user input, etc.) before handing over control. The program is then suspended until the next user request. When the user makes the next input, CICS re-launches the program from the point where it left off.
2. Efficiency in Resource Management: Since the program is not kept in memory between tasks, it frees up valuable system resources for other transactions. This "on-demand" nature of processing is what makes pseudo-conversational programming a hallmark of CICS — it ensures that resources are used efficiently and dynamically, only loading and executing the program when needed.
3. Re-Entrancy and State Recovery: CICS takes full advantage of its re-entrant program model. This means that multiple tasks can invoke the same program simultaneously, but each instance of the program is independent of the others. CICS ensures that each user’s state is isolated, even when the same program code is being executed in parallel.
4. Transaction Control (Transid): Every time the program returns control to CICS after completing a task, a transaction identifier (transid) is issued, which acts as a kind of "bookmark" for the state of that particular task. This ensures that the system knows exactly where to resume the program from once the user takes their next action. The transid is crucial in tracking the flow of a transaction, even if the program is invoked multiple times during its lifecycle.
5. Recovery and Continuity: One of the key features of CICS pseudo-conversational programming is the ability to handle interruptions and failures gracefully. If the system or program encounters an error or if the user session is disconnected, CICS can recover the program's state and restart the task from a previous valid point. This robustness is critical for applications that require high availability and fault tolerance, such as banking systems and ATMs.
The Beauty of CICS Pseudo-Conversational Programs
The real beauty of pseudo-conversational programs in CICS lies in their efficiency and scalability. By releasing program control after each task, the system can handle a large volume of concurrent transactions without overwhelming system resources. This is particularly advantageous in scenarios where each transaction might take varying amounts of time or require different amounts of system resources.
Moreover, pseudo-conversational programs make it easier for developers to design modular, maintainable code. By structuring the application as discrete steps, each with a well-defined purpose, the program becomes more understandable and easier to debug, as compared to continuous, monolithic code.
Why Pseudo-Conversational Programs Are Still Relevant
In the age of cloud computing, containerized microservices, and real-time data processing, it might seem like pseudo-conversational programs are a concept destined for obsolescence. However, when viewed through the lens of modern computing challenges, pseudo-conversational programs reveal themselves as a timeless solution with unique advantages:
1. Low Latency, High Throughput: CICS excels in environments where low-latency processing and high throughput are paramount. Its ability to execute discrete transactions quickly, and only load necessary resources when needed, provides a level of efficiency that modern cloud systems may struggle to replicate without extensive overhead.
2. Reliability and Availability: When it comes to mission-critical systems, such as ATMs, banking systems, and airline reservation platforms, uptime and reliability are non-negotiable. CICS’s re-entrant design and ability to manage thousands of concurrent tasks with minimal resource usage ensures the system is highly available and resilient to failure.
3. Transaction Integrity: In environments where transactions must be atomic and recoverable, CICS’s built-in capabilities to maintain consistency across distributed systems make it an irreplaceable part of the financial and transactional world.
4. Seamless Integration with Legacy Systems: Modern enterprises often face the challenge of integrating cloud-based applications with their legacy systems. CICS programs, particularly pseudo-conversational ones, have proven to be resilient and adaptable when integrated with newer technologies, making them indispensable in hybrid cloud environments.
5. Cost Efficiency: While migrating to the cloud may bring scalability benefits, it also incurs costs in terms of compute, storage, and network usage. CICS’s on-demand processing model is inherently cost-effective, allowing organizations to scale with minimal resource expenditure — a quality not always easily replicated in the cloud.
The Future of Pseudo-Conversational Programming in CICS
As organizations continue to migrate to cloud-based systems and embrace DevOps, containerization, and microservices, the underlying principles of CICS pseudo-conversational programming may still offer lessons in efficiency and resource management. There may be opportunities to reimagine this paradigm in the context of distributed and cloud-native architectures, with concepts such as "statelessness," "event-driven processing," and "serverless computing" offering modern-day equivalents of CICS’s elegant design.
While CICS’s pseudo-conversational programs are deeply tied to the mainframe ecosystem, the principles they espouse — optimizing resource usage, minimizing latency, ensuring transaction integrity, and providing robustness — are universal. As industries shift to cloud architectures, the need for efficient transaction management will remain, and the legacy of CICS can inspire the development of future systems that continue to balance flexibility, performance, and reliability.
Conclusion
CICS pseudo-conversational programs remain a cornerstone of transactional processing, providing an elegant solution to the challenges of handling thousands of concurrent tasks with minimal resource consumption. Their unique combination of re-entrancy, state preservation, and efficiency ensures they continue to serve mission-critical applications in industries around the globe.
In an era where cloud computing and "modernization" are often synonymous with the abandonment of legacy systems, it is crucial to remember that there are timeless, proven approaches that continue to offer remarkable value. The beauty of CICS pseudo-conversational programs lies not only in their technical sophistication but in their enduring ability to deliver reliable, high-performance solutions for the most demanding transactional environments.
As the world continues to embrace new technologies, the legacy of CICS stands as a testament to the lasting power of intelligent, efficient design. The principles behind pseudo-conversational programming will undoubtedly continue to shape the future of computing, regardless of the platform or architecture employed.
Comparison of Pseudo-Conversational Programs vs Conversational Programs
In the context of CICS (Customer Information Control System), both pseudo-conversational and conversational programs serve the purpose of processing transactions, but they differ in how they handle interaction between the user, system, and program. Below is a concise comparison of these two types of programs:
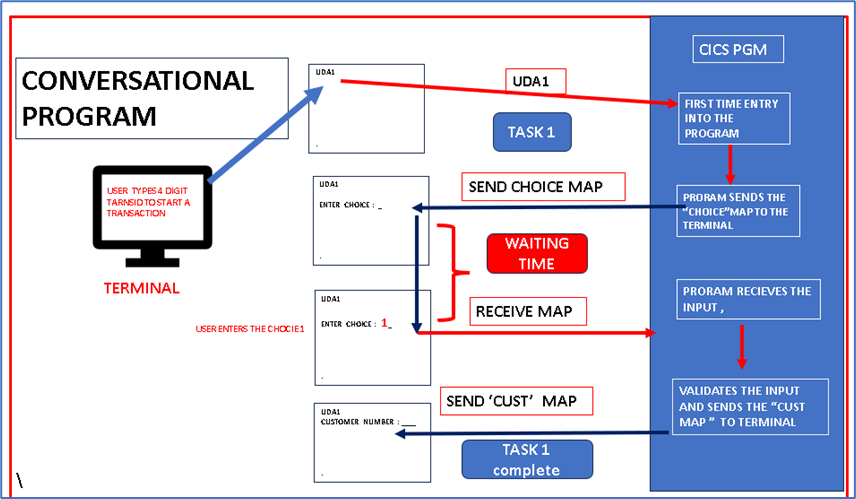
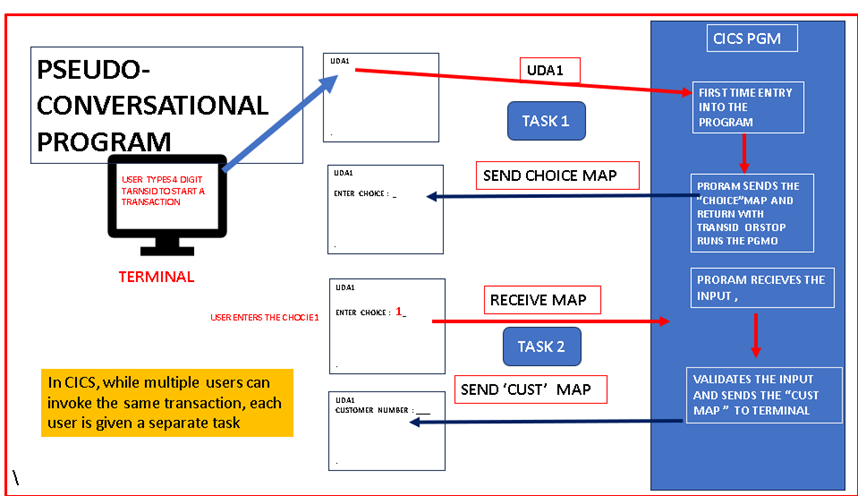
1. Program Lifecycle and Interaction
- Conversational Program:
- The program remains active and resident in memory for the entire duration of the interaction between the user and the system.
- The user’s input is processed in a continuous cycle without interruptions, where the program waits for input, processes it, and returns results in real-time.
- Example: A traditional online banking session where the program stays active during the entire transaction until completed.
- Pseudo-Conversational Program:
- The program is invoked for each transaction step but is suspended after completing a task.
- After each task, the program relinquishes control back to CICS, which stores the transaction’s state, allowing the program to resume from where it left off once the user provides further input.
- Example: ATM transactions, where each step (e.g., card validation, PIN entry, withdrawal) involves the program being invoked multiple times.
2. Resource Utilization
- Conversational Program:
- Since the program remains in memory for the entire duration of the interaction, it consumes system resources (memory, CPU) throughout the session.
- This can result in higher resource usage, especially if the program is managing long or complex user sessions.
- Pseudo-Conversational Program:
- The program only uses resources during active execution and is suspended (not in memory) between steps.
- This reduces memory and CPU consumption, allowing CICS to handle many concurrent tasks more efficiently.
3. Scalability and Concurrency
- Conversational Program:
- Not as scalable in environments where multiple concurrent users are interacting with the system, as the program has to stay in memory for each user session.
- May lead to resource contention, especially in high-traffic systems.
- Pseudo-Conversational Program:
- More scalable because programs do not remain in memory after completing a task.
- CICS can handle many more concurrent users by re-invoking the program as needed, thus improving overall scalability and resource optimization.
4. Fault Tolerance and Recovery
- Conversational Program:
- In case of failure or system crash, the program may lose its state since it is active throughout the entire interaction.
- Recovery requires the entire session to be restarted from the beginning, as the program has to be re-invoked with a fresh state.
- Pseudo-Conversational Program:
- The state of the program is saved at each step (using transaction IDs), allowing the program to resume where it left off if there’s an interruption or failure.
- This results in higher fault tolerance and smoother recovery, particularly in mission-critical environments.
5. Example Use Cases
- Conversational Program:
- Long-running user sessions like batch programs (e.g., complex data entry or real-time data analytics).
- Systems where user interaction is constant and uninterrupted (e.g., customer service applications, call center systems).
- Pseudo-Conversational Program:
- Systems that need to process discrete steps with intermittent user input (e.g., ATM transactions, online banking).
- Environments where high transaction volume and efficient resource management are critical (e.g., financial transactions, reservations).
Summary of Key Differences:
|
Aspect |
Conversational Program |
Pseudo-Conversational Program |
|
Program Lifecycle |
Runs continuously, active throughout the interaction |
Invoked per tasks, suspends between user actions |
|
Resource Utilization |
Higher, since the program stays in memory |
Lower, program suspended after each step |
|
Scalability |
Less scalable, may cause resource contention |
Highly scalable, better suited for concurrent tasks |
|
Fault Tolerance |
Limited, requires restart if session fails |
High, can resume from where it left off with state preservation |
|
Use Cases |
Long-running sessions, continuous interaction (e.g., call centers) |
Short, discrete tasks with intermittent input (e.g., ATMs) |